Troubleshooting Provider Appliance
Contents
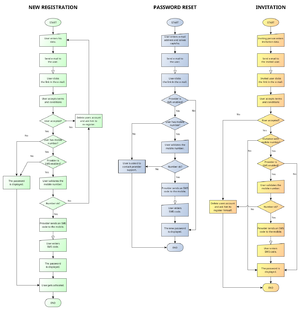
Process of registration,invitation and password reset
The following chart shows you the different processes in simplified manner (click to zoom in):
-
Common messages in appliance error log
Clearing Related
CRIT: Error executing curl call. Error:connect() timed out! [funcHtmlAndBrowser.php/PostRequest] CRIT: Locked connection-id 1. Check /opt/provider/REGIFY_INCLUDE/../ClearingLock.dat [funcClearing.php/LockClearingConnectionID] CRIT: clearing connection 1 not available [/]
This happens if a clearing connection was not functional. Most providers today are using two connections (1 and 2). In this case, the connection 1 failed to connect to the clearing. The connection got locked and is no longer used. Every five minutes, the provider appliance try's to re-use such locked connections. If they are working, they will get un-locked automatically.
CRIT: No more clearing connections available. Set provider to maintain-mode... [funcClearing.php/GetClearingConnectionID]
This means that no more functional clearing connection is available. In this case, the regify provider appliance automatically enters the maintenance mode.
WARN: removed maintenance-state of provider [phpFailoverCheck.php/RemoveMaintenanceFile]
This message indicates that the provider has been in maintenance mode before. If the provider appliance finds out that at least one clearing connection is functional again, the maintenance mode is removed automatically and this message is triggered.
WARN: all clearing connections are reactivated now [/]
This means that all defined clearing connections are found as working (mostly after one or more connections have been locked before).
Security Related
PHP Warning: session_destroy(): Trying to destroy uninitialized session in /opt/provider/REGIFY_PUBLIC/ADMINISTRATION/index.php on line X
This happens sometimes if some administrators session ran out of time and he then clicked on some administration function link. You can ignore this message.
PHP Warning: pack(): Type H: illegal hex digit X in /opt/provider/common/incSecurity.php on line X
This message sometimes happened in provider appliance V3.2 and V3.3. It happens if the regify provider appliance gets some invalid URL calls with hex encoded values that contain non-hex characters. It seems like the result of some special hacking event by automatic hacking scripts testing random sites.
CRIT: Access blocked (PHPIDS treshold X reached) for the following request: ------------------------------------------------------------------------------------------- Security Alert (PHPIDS): IMPACT: 36 TAGS: xss, csrf, id, rfe, lfi URL: /XXXXX.php........ ...
This means that the internal IDS (Intrusion Detection System) found something suspicious and blocked this call. The value behind IMPACT: shows you how dangerous the attack was. Values between 16 and 35 are lower potential, higher values are mostly some serious attack. This message is followed by the parameters (PARAMETERS: and FIELDS:) that lead to the alert showing you all fields and values received during the attack. If you consider these values as very suspicious or you have repeating alerts, please contact regify support and send us the complete log information.
CRIT: Wrong session-host for url /downloads.php?lg=EN / /downloads.php called by xxx
We currently do not know the origin of this problem. It looks like someone with an old cookie (maybe wrong system time) is trying to connect to your provider with this old cookie. As the session is already finished on the provider, this entry is created. You can ignore this. But if you know the origin of this, please contact us. We are interested in investigating this issue.
PHP Warning: session_start(): The session id is too long or contains illegal characters, valid characters are a-z, A-Z, 0-9... PHP Warning: Unknown: The session id is too long or contains illegal characters, valid characters are a-z, A-Z, 0-9... PHP Warning: Unknown: Failed to write session data (files). Please verify that the current setting of session.save_path is correct PHP Warning: Unknown: Input variables exceeded 1000.
All these entries are coming from intrusion attempts by hackers. Mostly some hacker-tools are testing if systems are vulnerable on such attacks. Currently, the regify provider is not affected but it triggers such kind of entries. You can ignore and delete such entries.
Other log entries
PHP Warning: htmlentities(): Invalid multibyte sequence...
This happens more often since provider V3.4.0. We are investigating the problem.
Handle known appliance problems
The web server does not start with an error message like this:
(98)Address already in use: make_sock: could not bind to address 0.0.0.0:80
This means, that some httpd processes are hanging. Please use the following to identify the processes:
[root@clearing ~]# ps -ax | grep httpd 22680 ? S 0:06 /usr/sbin/httpd -k start 22681 ? S 0:03 /usr/sbin/httpd -k start 22682 ? S 0:05 /usr/sbin/httpd -k start
In this case, three processes hanging. To get rid of them, try to kill the first one with the lowest process id (22680):
[root@clearing ~]# kill 22680
Check, if the others are also gone. If not, repeat this with the other process id's, too. If all httpd entries are gone, start the webserver using
[root@clearing ~]# apachectl start
Handle known Internet Explorer issues
Under certain conditions conditions Microsoft IE version 10 and below will interpret webpages as an outdated version of IE. In some cases it interprets webpages as Internet Explorer version 7. This will cause the provider to work incorrectly since regify support IE8 and later.
Is there a fix for this?
Yes, the next provider update will solve this issue by forcing your browser to always interpret pages in "Standard Document Mode".
Until the next update is available, the following manual fix can be applied:
1- While in the browser, press F12 on your keyboard to start Internet Explorer developer tools.
2- Developer tools panel will appear. Press on document Mode and select the "Standards" option.
What parts of the provider website are affected?
We have received several calls from clients concerning the issue. All of them have pointed out that the group management page is not working properly.
However any JavaScript powered page can be effected by this issue.
What about future Internet Explorer version?
Microsoft has decided to force their browsers to follow the web standards starting from IE version 11 and greater.
What about other browsers?
Other browsers follow standards, therefore they are not effected by the issue.
Why does not regify support Internet Explorer 7?
Internet Explorer is an outdated browser that does not follow web standards. Its usage has dropped to less than 1 percent this year.